网络入侵检测系统之 Suricata(七)--DDOS 流量检测模型

Suricata 支持 DDOS 流量检测模型
What
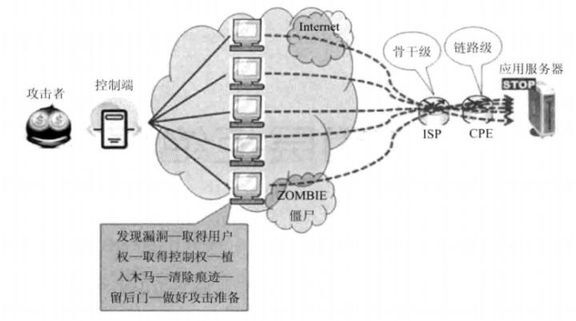
分布式拒绝服务(Distributed Denial of Service,简称 DDoS)将多台计算机联合起来作为攻击平台,通过远程连接利用恶意程序,对一个或多个目标发起 DDoS 攻击,消耗目标服务器性能或网络带宽,从而造成服务器无法正常地提供服务。
How
通常,攻击者使用一个非法账号将 DDoS 主控程序安装在一台计算机上,并在网络上的多台计算机上安装代理程序。在所设定的时间内,主控程序与大量代理程序进行通讯,代理程序收到指令时对目标发动攻击,主控程序甚至能在几秒钟内激活成百上千次代理程序的运行。
Classification

Suricata Rules
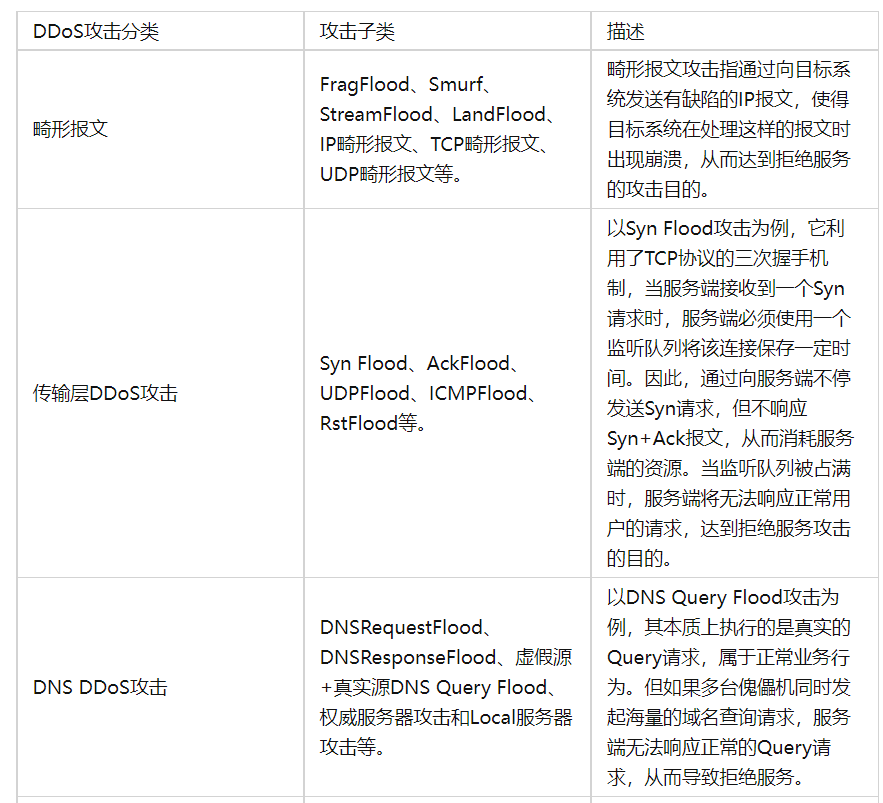
tcp 畸形报文
TCP 报文标志位包括 URG、ACK、PSH、RST、SYN、FIN。攻击者通过发送非法 TCP flag 组合的报文,受害主机收到后进行判断识别,消耗其性能,甚至会造成有些操作系统报文处理异常,主机崩溃。
alert tcp $EXTERNAL_NET any -> $HOME_NET any (msg:"GPL SCAN nmap fingerprint attempt"; flags:SFPU; flow:stateless; reference:arachnids,05; classtype:attempted-recon; sid:2100629; rev:7; metadata:created_at 2010_09_23, updated_at 2010_09_23;)
teardrop 攻击
攻击者截取 IP 数据包后,把偏移字段设置成不正确的值,接收端在收到这些分拆的数据包后,就不能按数据包中的偏移字段值正确组合出被拆分的数据包,这样,接收端会不停的尝试,以至操作系统因资源耗尽而崩溃
alert tcp $EXTERNAL_NET any -> $HOME_NET any (msg:"ET EXPLOIT Invalid non-fragmented packet with fragment offset>0"; fragbits: !M; fragoffset: >0; reference:url,http://doc.emergingthreats.net/bin/view/Main/2001022; classtype:bad-unknown; sid:2001022; rev:5; metadata:created_at 2010_07_30, updated_at 2010_07_30;)
smurf 攻击
攻击者向网络中的广播地址发送源 IP 伪造为受害者的 ICMP 请求报文,使得网络中的所有主机向受害者回应 ICMP 应答报文,这样造成受害者系统繁忙,链路拥塞
alert ip any any <> 127.0.0.0/8 any (msg:"GPL SCAN loopback traffic"; reference:url,http://rr.sans.org/firewall/egress.php; classtype:bad-unknown; sid:2100528; rev:6; metadata:created_at 2010_09_23, updated_at 2020_08_20;)
land 攻击
Land 攻击是指攻击者向受害者发送 TCP 报文,此 TCP 报文的源地址和目的地址同为受害者的 IP 地址。这将导致受害者向它自己的地址发送 SYN-ACK 回应报文,结果这个地址又发回 ACK 消息并创建一个空连接。从而造成资源的消耗。
alert tcp $HOME_NET any -> $HOME_NET any (msg:"ET MALWARE APT 41 LOWKEY Backdoor [TCP Relay Module] - TCP Relay Successfully Activated on New Host"; flow:established,to_server; content:"|00 00 00 00 00 D4 00 00 00 00 00 00 00 00 00 00|"; reference:url,http://www.fireeye.com/blog/threat-research/2019/10/lowkey-hunting-for-the-missing-volume-serial-id.html; classtype:command-and-control; sid:2028888; rev:1; )
ping of death
攻击者 A 向受害者 B 发送一些尺寸超大的 ICMP
alert icmp $EXTERNAL_NET any -> $HOME_NET any (msg:"GPL ICMP Large ICMP Packet"; dsize:>800; itype:8; reference:arachnids,246; classtype:bad-unknown; sid:2100499; rev:5; metadata:created_at 2010_09_23, updated_at 2010_09_23;)
syn flood
恶意的向某个服务器端口发送大量的 SYN 包,则可以使服务器打开大量的半开连接,分配 TCB,从而消耗大量的服务器资源,同时也使得正常的连接请求无法被响应。而攻击发起方的资源消耗相比较可忽略不计。
alert tcp $EXTERNAL_NET 10000: -> $HOME_NET 0:1023 (msg:"ET DOS Potential Tsunami SYN Flood Denial Of Service Attempt"; flags:S; flow:to_server; dsize:>900; threshold: type both, count 20, seconds 120, track by_src; reference:url,http://security.radware.com/uploadedFiles/Resources_and_Content/Threat/TsunamiSYNFloodAttack.pdf; classtype:attempted-dos; sid:2019404; rev:3; metadata:created_at 2014_10_15, updated_at 2014_10_15;)
udp flood
UDP Flood 属于带宽类攻击,向目标服务器发起大量的 UDP 报文,这种 UDP 报文通常为大包,且速率非常快,通常会造成以下危害:消耗网络带宽资源,严重时造成链路拥塞;大量变源变端口的 UDP Flood 会导致依靠会话转发的网络设备,性能降低甚至会话耗尽,从而导致网络瘫痪。
alert udp $EXTERNAL_NET any -> $HOME_NET 5060 (msg:"ET VOIP INVITE Message Flood UDP"; content:"INVITE"; depth:6; threshold: type both , track by_src, count 100, seconds 60; reference:url,http://doc.emergingthreats.net/2009698; classtype:attempted-dos; sid:2009698; rev:1; metadata:created_at 2010_07_30, updated_at 2010_07_30;)
icmp flood
短时间内向特定目标不断请求 ICMP 回应,致使目标系统负担过重而不能处理合法的传输任务,就发生了 ICMP Flood。
alert icmp any any -> any any (msg:"ET DOS Microsoft Windows 7 ICMPv6 Router Advertisement Flood"; itype:134; icode:0; byte_test:1,&,0x08,2; content:"|03|"; offset:20; depth:1; byte_test:1,&,0x40,2,relative; byte_test:1,&,0x80,2,relative; threshold:type threshold, track by_src, count 10, seconds 1; reference:url,http://www.samsclass.info/ipv6/proj/proj8x-124-flood-router.htm; classtype:attempted-dos; sid:2014996; rev:3; metadata:created_at 2012_07_02, updated_at 2012_07_02;)
dns quert flood
多台傀儡机同时发起海量的域名查询请求,服务端无法响应正常的 Query 请求,从而导致拒绝服务。
alert dns $HOME_NET any -> any any (msg:"ET MALWARE Likely Linux/Tsunami DDoS Attack Participation (s-p-o-o-f-e-d.h-o-s-t.name)"; threshold:type limit,track by_src,count 3,seconds 60; dns.query; content:"s-p-o-o-f-e-d.h-o-s-t.name"; depth:26; fast_pattern; nocase; endswith; reference:md5,c01991d55133d0057c9b721bb141a5d9; classtype:trojan-activity; sid:2021691; rev:5; metadata:created_at 2015_08_19, former_category CURRENT_EVENTS, updated_at 2020_09_17;)
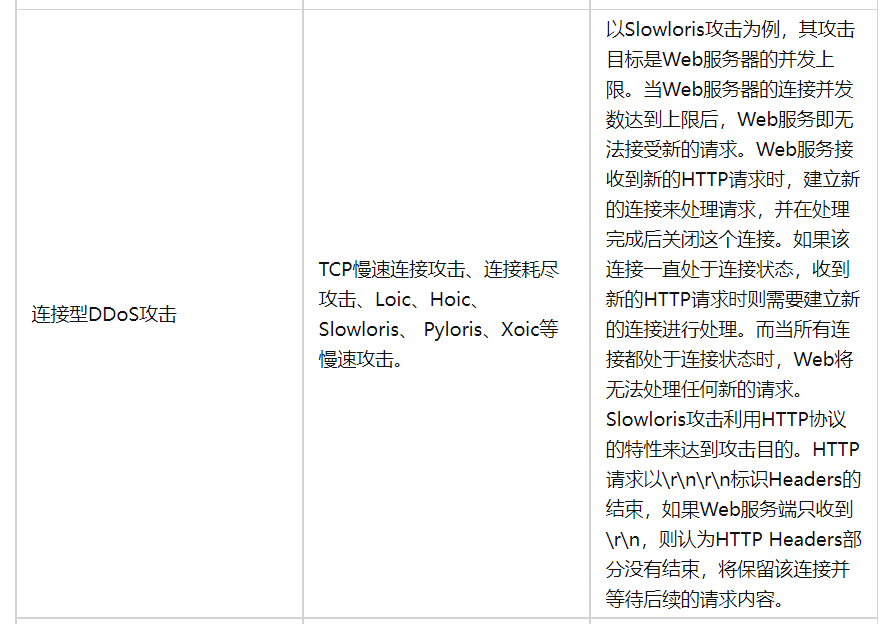
slowloris
攻击者在 HTTP 请求头中将 Connection 设置为 Keep-Alive,要求 Web Server 保持 TCP 连接不要断开,随后缓慢的每隔几分钟发送一个 key value 格式的数据到服务端,如 a:b\r\n,导致服务端认为 HTTP 头部没有接收完成而一直等待。如果攻击者使用多线程或者傀儡机来做同样的操作,服务器的 WEB 容器很快就被攻击者占满了 TCP 连接而不再接受新的请求。
alert http $EXTERNAL_NET any -> $HTTP_SERVERS any (msg:"ET SCAN Simple Slowloris Flooder"; flow:established,to_server; threshold:type limit, track by_src, count 1, seconds 300; http.method; content:"POST"; http.header; content:"Content-length|3a 20|5235|0d 0a|"; fast_pattern; http.header_names; content:!"User-Agent|0d 0a|"; reference:url,http://www.imperva.com/docs/HII_Denial_of_Service_Attacks-Trends_Techniques_and_Technologies.pdf; classtype:web-application-attack; sid:2016033; rev:5; metadata:created_at 2012_12_13, updated_at 2020_05_08;)
cc 攻击
针对 Web 服务在第七层协议发起的攻击,正常的有效的数据包 不断发出针对不同资源和页面的 HTTP 请求,并尽可能请求无法被缓存的资源(DB 查询等),这样就极大加重了服务器的计算和 IO 资源,从而导致瘫痪
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"ET DOS LOIC Javascript DDoS Outbound"; flow:established,to_server; threshold: type both, track by_src, count 5, seconds 60; http.method; content:"GET"; http.uri; content:"/?id="; fast_pattern; depth:5; content:"&msg="; distance:13; within:5; pcre:"/^\/\?id=[0-9]{13}&msg=/"; reference:url,http://isc.sans.org/diary/Javascript+DDoS+Tool+Analysis/12442; reference:url,http://www.wired.com/threatlevel/2012/01/anons-rickroll-botnet; classtype:attempted-dos; sid:2014141; rev:6; metadata:created_at 2012_01_23, updated_at 2020_05_06;)
Suricata 支持 ddos 流量模型的 Option
tcp.flags
fragbits,fragoffset
itype, icode
flow
threshold
byte_test
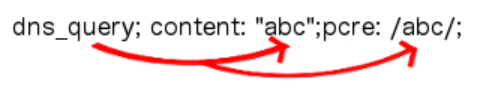
dns.query,http.header,http.method,http.uri
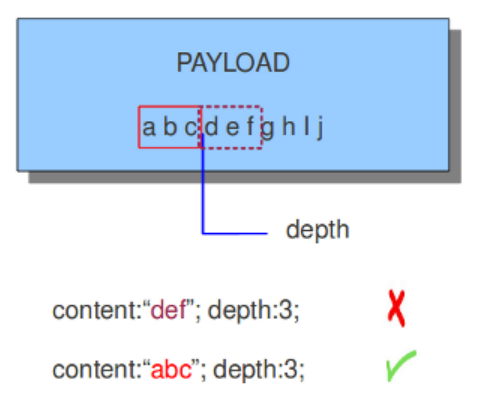
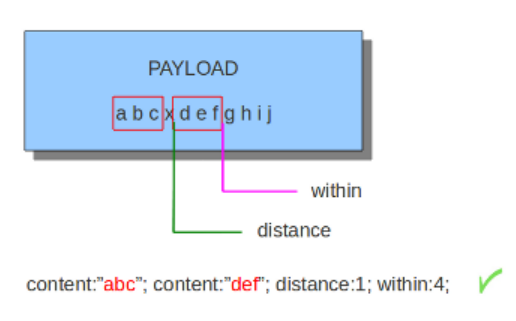
dsize,depth,distance,within
Reference
版权声明: 本文为 InfoQ 作者【于顾而言】的原创文章。
原文链接:【http://xie.infoq.cn/article/d8edf2e4c0022f1541824b97e】。文章转载请联系作者。








评论