Spring Boot 集成 Spring Security 之 HTTP 请求授权
一、HTTP 请求授权工作原理
基于 Spring Security 最新的 Http 请求授权讲解,不再使用旧版的请求授权
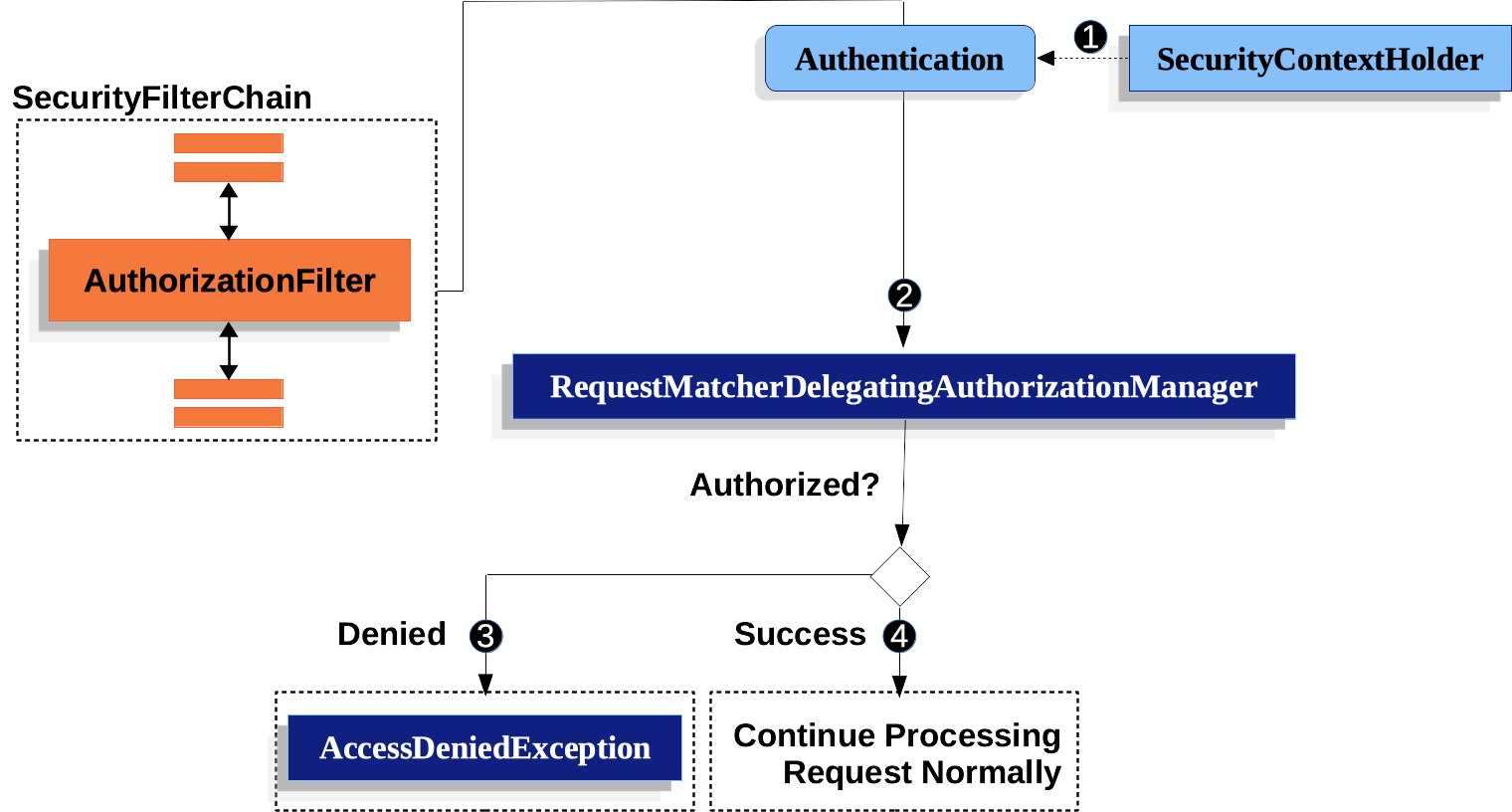
授权过滤器 AuthorizationFilter 获取认证信息
调用 RequestMatcherDelegatingAuthorizationManager 的 check 方法验证该用户是否具有该请求的授权
RequestMatcherDelegatingAuthorizationManager 根据配置的请求和授权关系校验用户是否具有当前请求的授权并返回授权结果
AuthorizationFilter 处理授权结果,授权成功则继续调用过滤器链,否则抛出 AccessDeniedException 异常
认证失败时,ExceptionTranslationFilter 处理 AccessDeniedException 异常,如果是当前认证是匿名认证或者 RememberMe 认证则调用 AuthenticationEntryPoint 的 commence 方法,否则调用 AccessDeniedHandler 的 handler 方法
工作原理图如下
二、HTTP 请求授权配置
1、添加用户权限
2、配置 ExceptionTranslationFilter 自定义异常处理器
因 AuthorizationFilter 授权失败时会抛出异常,该异常由 ExceptionTranslationFilter 处理,所以要配置自定义的异常处理器。
自定义 AccessDeniedHandler 和 AuthenticationEntryPoint 异常处理器(可以用一个类实现认证授权相关的所有接口,也可以使用多个类分别实现)。
配置异常处理:
3、HTTP 请求授权配置
本文使用最新的 authorizeHttpRequests(AuthorizationFilter+AuthorizationManager)配置,不在使用 authorizeRequests(FilterSecurityInterceptor+AccessDecisionManager+AccessDecisionVoter)
请求和授权配置成对出现,配置在前的优先级更高
请求种类 antMatchers:Ant 风格的路径模式,
?(匹配一个字符)、*(匹配零个或多个字符,但不包括目录分隔符)、**(匹配零个或多个目录)mvcMatchers:Spring MVC 的路径模式,支持路径变量和请求参数 regexMatchers:正则表达式路径模式 requestMatchers:实现 RequestMatcher 自定义匹配逻辑 anyRequest:未匹配的其他请求,只能有一个且只能放在最后授权种类 permitAll:匿名或登录用户都允许访问 denyAll:匿名和登录用户都不允许访问 hasAuthority:有配置的权限允许访问,AuthorityAuthorizationManager 校验 hasRole:有配置的角色允许访问,ROLE_{配置角色}与用户权限匹配,AuthorityAuthorizationManager 校验 hasAnyAuthority:有配置的任意一个权限的允许访问,AuthorityAuthorizationManager 校验 hasAnyRole:有配置的任意一个角色允许访问,ROLE_{配置角色}与用户权限匹配,AuthorityAuthorizationManager 校验 authenticated:已认证(不包括匿名)的允许访问,AuthenticatedAuthorizationManager 校验 access:自定义授权处理
因 authorizeHttpRequests 不支持使用 anonymous()的方式配置匿名访问,未自定义匿名角色时可以通过 hasRole("ANONYMOUS")或者 hasAuthority("ROLE_ANONYMOUS")或其他类似的方式实现允许匿名请求的设置

http 请求授权配置
完整过滤器链配置
三、测试接口
1、测试类
2、测试
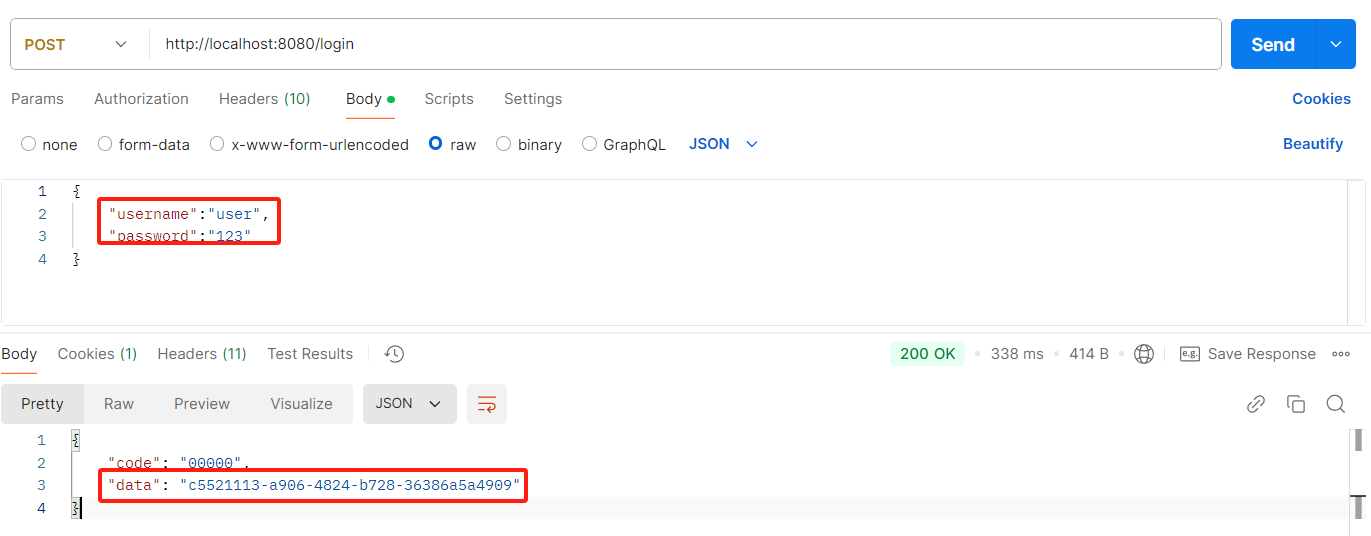
1、登录获取 token
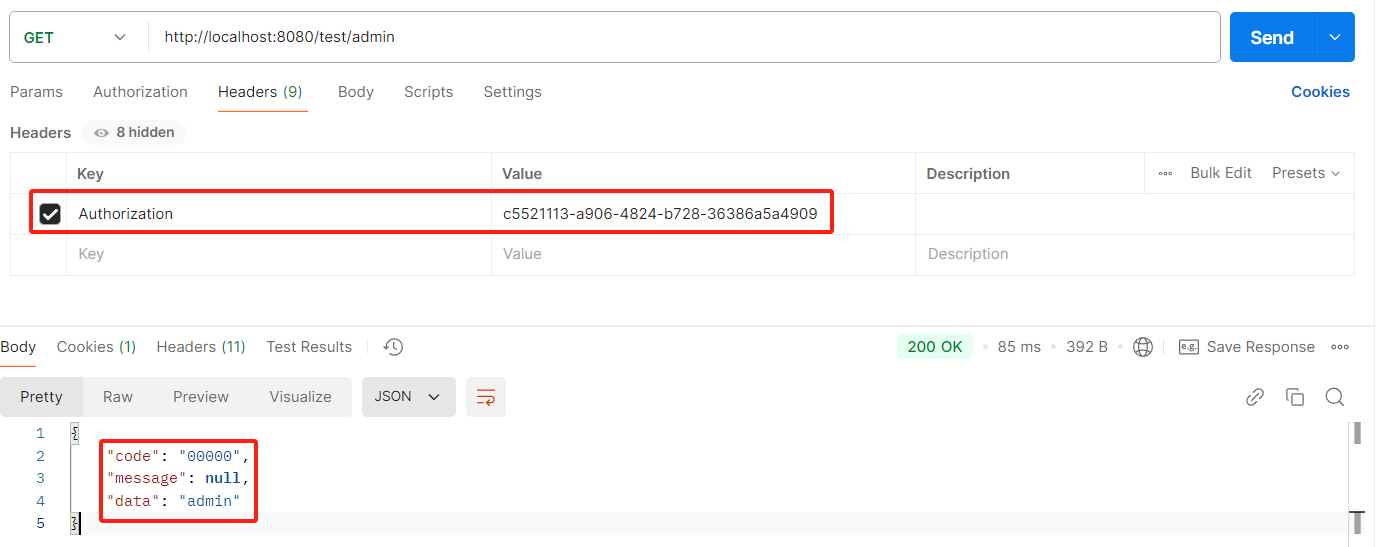
2、admin 接口测试
3、其他接口不在一一测试,有疑问或问题评论或私聊
四、总结
授权是拿用户的权限和可以访问接口的权限进行匹配,匹配成功时授权成功,匹配失败时授权失败
用户的权限对象是 SimpleGrantedAuthority,字符串属性 role
接口的 role 权限会通过 ROLE_{role}转化为 SimpleGrantedAuthority 及其字符串属性 role
接口的 authority 权限会直接转化为 SimpleGrantedAuthority 及其字符串属性 role
拥有 ROLE_ANONYMOUS 权限或者 ANONYMOUS 角色可以访问匿名接口
文章转载自:那你为何对我三笑留情










评论